Who’s Buying — and How Decisions Are Made
Cybersecurity buyers aren’t a monolith. Understand who’s involved in the purchase—and how decisions really happen.
✔ Who owns the final decision vs. who influences it
✔ What the buying cycle actually looks like today
✔ Which content formats buyers trust most
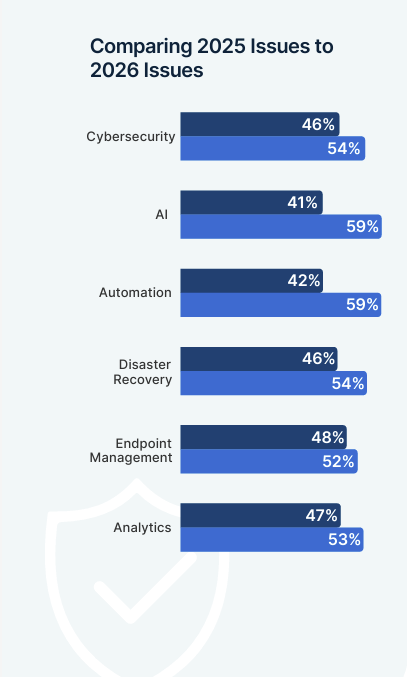
Security Priorities & Budget Allocation
See where cybersecurity budgets are being invested—and what’s rising to the top of the CISO agenda.
✔ Top areas of investment
✔ True CISO must-haves vs. nice-to-haves
✔ How economic pressure is reshaping security spend
The Channels That Actually Drive Results
Cut through the noise and focus on the channels that consistently engage cybersecurity buyers.
✔ Highest-performing content formats
✔ Most effective ad platforms and publishers
✔ The role of peer reviews, communities, and events
Messaging That Builds Trust
Learn what resonates with buyers—and what immediately turns them off.
✔ Messaging that earns credibility
✔ Gimmicks and buzzwords that no longer work
✔ Trust signals that influence real buying decisions
This isn’t just another industry overview.
It’s a practical playbook for cybersecurity marketers looking to sharpen their strategy, reach the right buyers, and turn insight into pipeline.